
Service insights
Speed is of the essence
I3 incident response and case management delivers the power
We found that whilst there are many incident management systems out there many of the options lacked key features, were slow, had unintuitive interfaces or were not security focussed.
So in 2016 we decided to build our own.
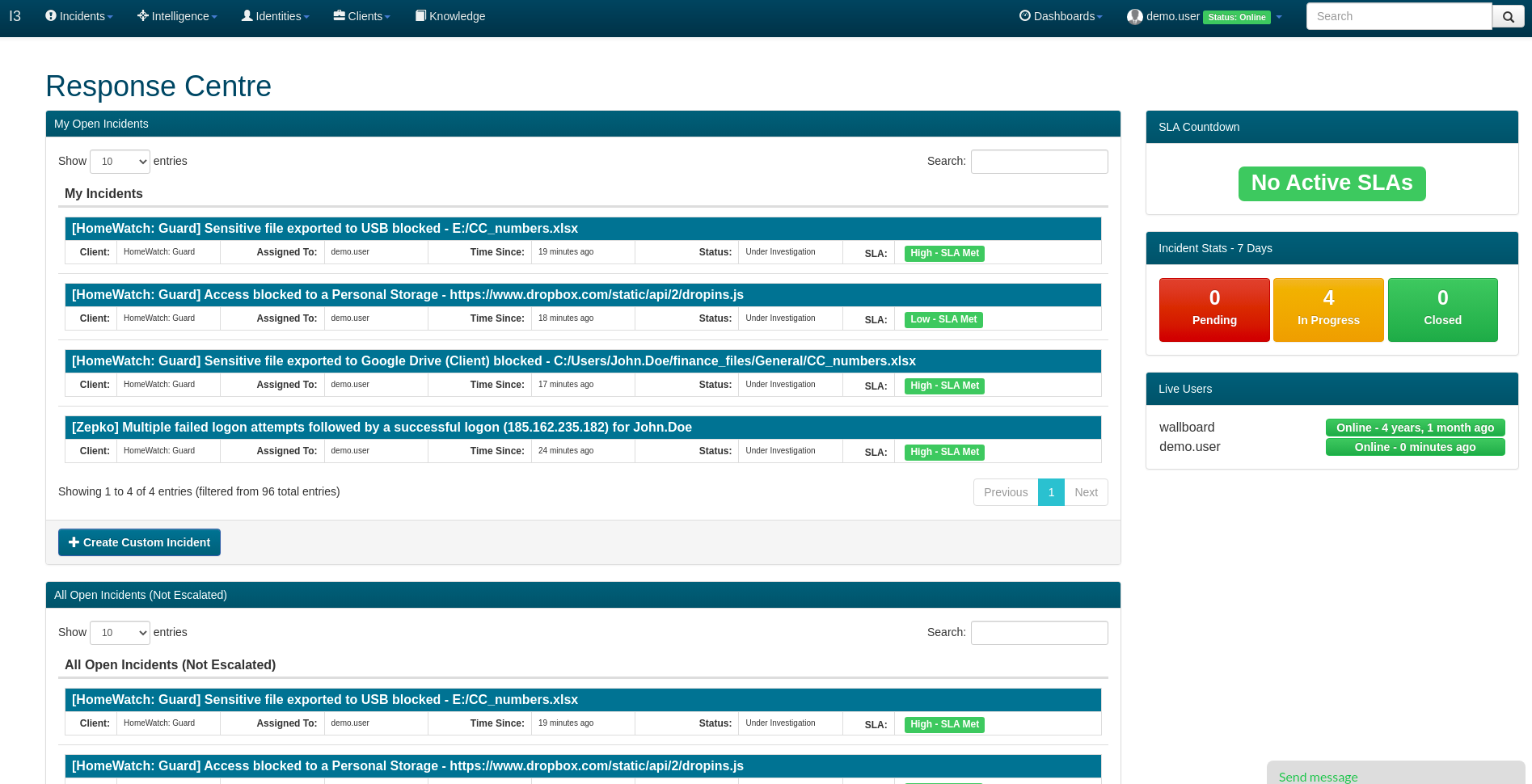
I3 is a security focussed incident management system designed by Zepko’s development team from the ground up focussing on Incidents, Identities and Intelligence.
This product offers many powerful features that enable the analyst team to work in a fast, effective and diligent manner including the following:
Related incident grouping
This allows the SOC to accurately group related incidents to ensure our customers security teams are not flooded with incidents and can see the important information quickly in cases where an attack has generated many incidents.
Live SLA Tracking
Our live Service Level Agreement tracker ensures the analyst team are always investigating incidents quickly, and our customers can see this in real time to provide assurance that we are on top of all security incidents.
Threat Intelligence Integration
Not only is our GTIN (Global Threat Intelligence Network) interface housed within the I3 portal, we have also integrated GTIN with every security incident upon creation.
I3 will automatically search our threat intelligence for any observables relating to a security incident, inform the analysts when one is present and provide a button to view the intelligence, but also to add the observable to GTIN when it is not yet present in the system.
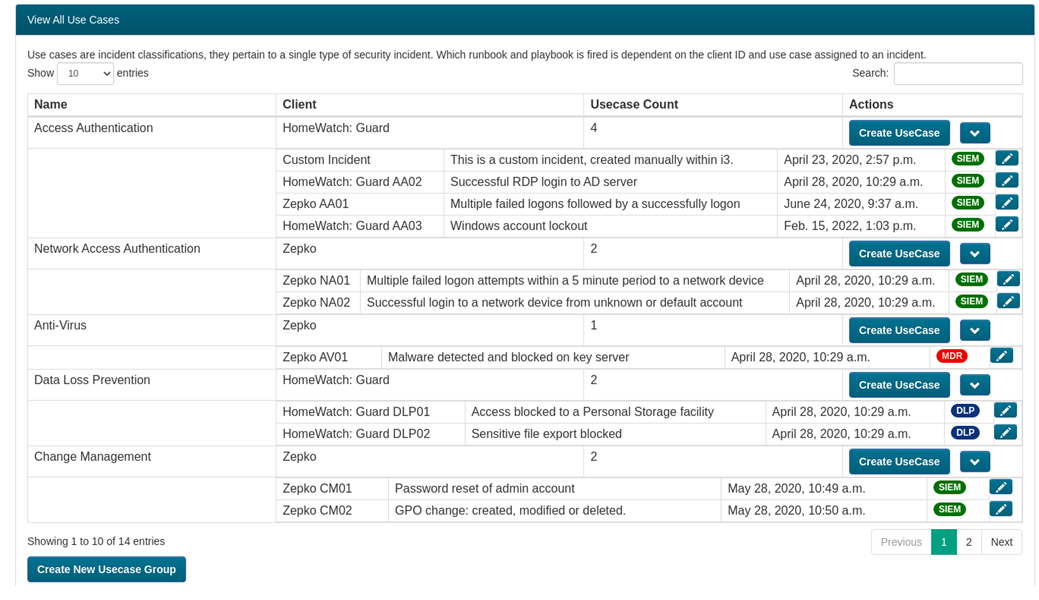
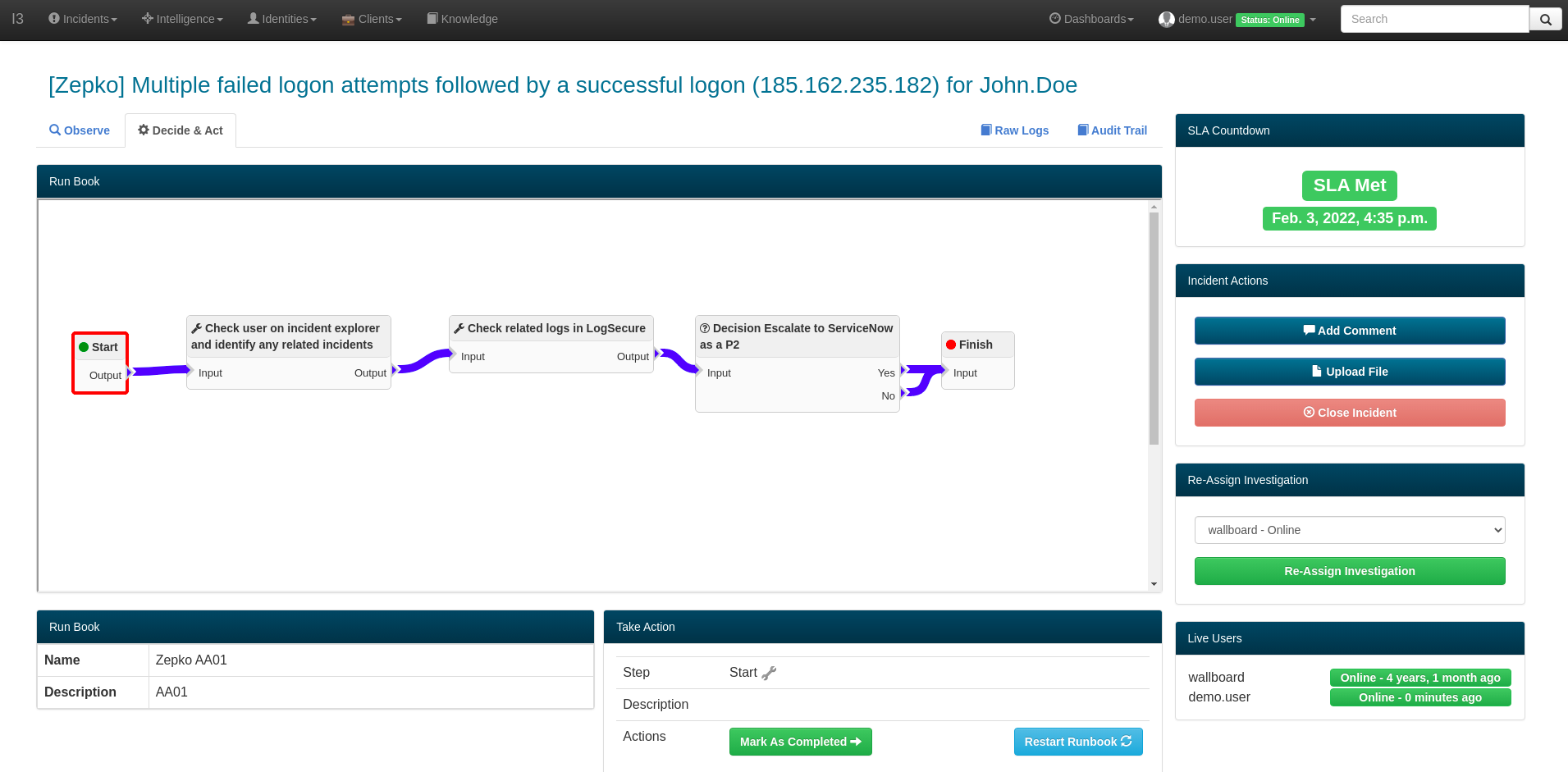
Integrated Runbooks
The runbook feature within I3 allows us to define investigation, escalation and resolution processes that are individually tracked and audited within each incident. Each customer’s runbooks are completely customizable on a use case to use case basis so you can always be sure that each incident is handled exactly how you want it to.
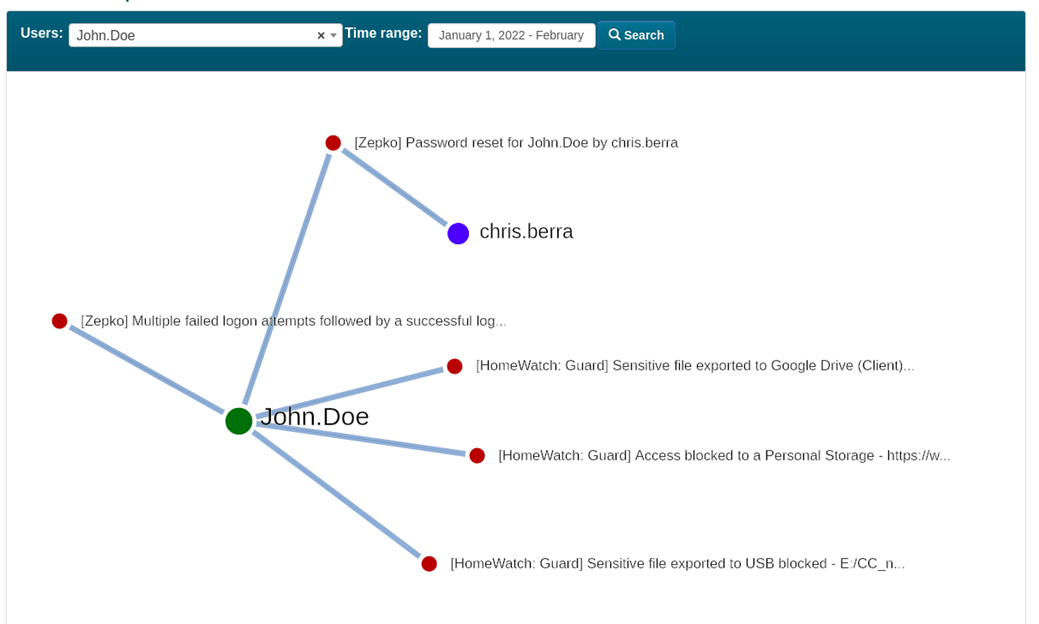
Incident Explorer
I3’s Incident Explorer feature allows the SOC team to pivot from key information such as user names within an incident using a slick visual interface to find more incidents within the specified time period relating to that user. At the click of a button the analysts can then pivot further from any new users identified in the results, quickly allowing the SOC to see the full scale and context of the activity behind security incidents.
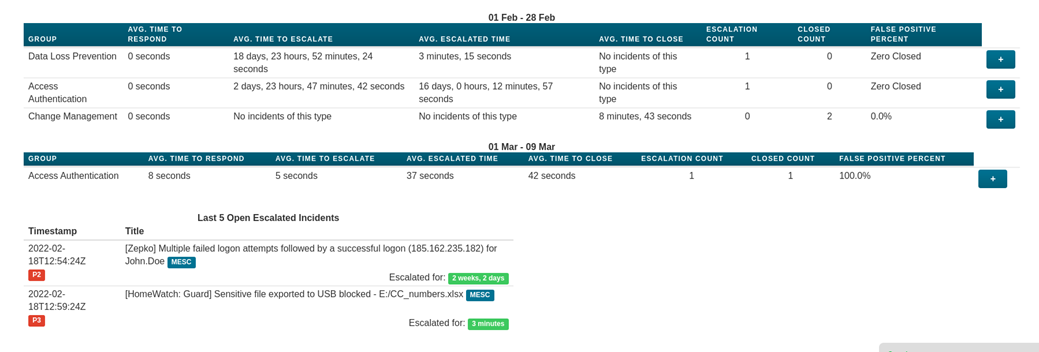
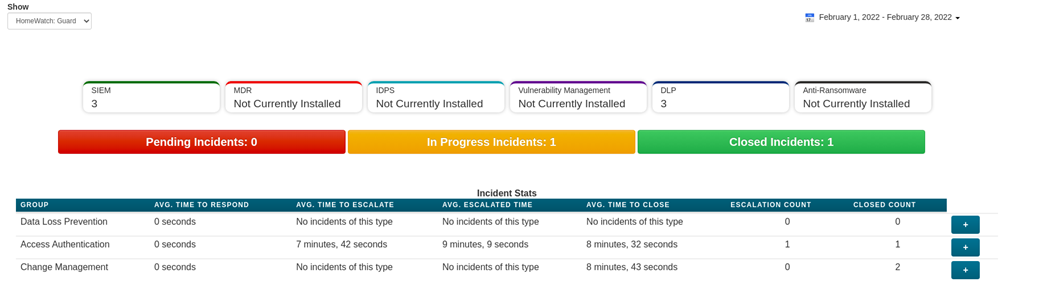
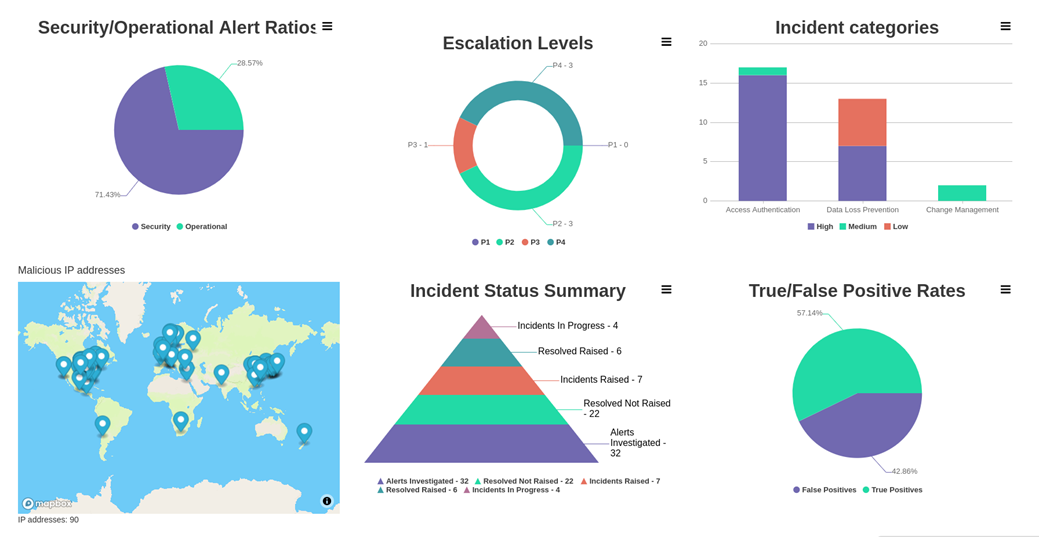
Incident Dashboards
I3 features responsive dashboards allowing you to quickly see the volume of security incidents, what types of incidents have been triggering, the true-to-false positive ratio and also which of your users have been triggering the most security alerts.
There are many more features in I3’s arsenal which make it one of the most powerful incident managements tools in the industry.
If you are interested in finding out more about I3, how we utilize it to protect our customers or any other services Zepko offer, get in touch today to arrange a demo.


