
Threat landscape
Threat Advisory – Office 365 MFA bypass
Office 365 MFA bypass via exploiting the end user
We have seen time and time again that attackers will constantly modify their tactics, techniques and procedures (TTP) to target the least patchable part of your security ecosystem, the human.
In a recent spate of attacks seen against organizations using Office 365, attackers are attempting to abuse the user-friendly features of MFA applications such as the Microsoft Authenticator App’s push notifications, which may not always provide detailed information such as the authentication source and also the alternate methods such as the phone call authentication option where Microsoft will phone the assigned phone number and ask the user to press the # key to approve the authentication.
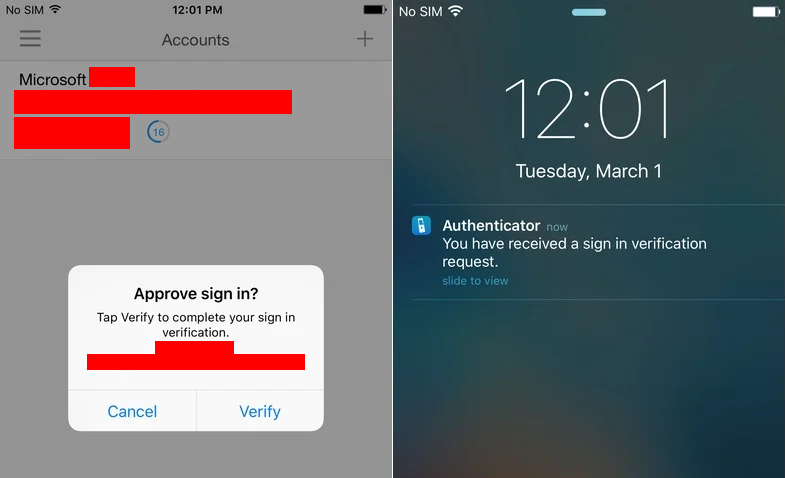
The attacker will couple these user-friendly features that do not require the entry of a code with attempting to authenticate at the start of business hours for the target organization.
Whilst technical users would spot this activity as suspicious, less tech savvy users have been tricked with this method many times as they may see the requests as normal activity or a quirk of the system not long after they have authenticated to work related systems.
Whilst no exploit is used and therefore no patch or fix for this can be issued, we recommend that a security bulletin is sent out to all end users to warn of this activity.
All end users should be wary of any MFA requests that they did not explicitly trigger themselves immediately as part of their authentication process and if there is any doubt, do not accept the authentication request and seek the assistance of the IT department to double check the authenticity.
This attack vector does not apply to code-entry MFA applications such as Google Authenticator and recently has only been seen targeting Office 365 accounts, but this bulletin is applicable to any use of MFA and users should also be warned against providing any MFA code to another individual as this should never be necessary for an IT department to ask their end users for.
Whilst patch management processes will capture keeping your software and firmware up to date, you must also ensure your end users are kept up to date as it is a combination of people, process and technology that will protect your organization.


